API Gateway & Step Function & Cognito
API Gateway
Serverless REST APIs
Invoke Lambda functions using REST APIs (API gateway will proxy the request to lambda)
AWS Lambda + API Gateway: No infrastructure to manage
Supports WebSocket (stateful)
Handle API versioning (v1, v2…), handle different environments (dev, test, prod…), handle security (Authentication and Authorization)
Rate Limiting (throttle requests) - returns 429 Too Many Requests
Cache API responses
Transform and validate requests and responses
Can be integrated with any HTTP endpoint in the backend or any AWS API
We can use an API Gateway REST API to directly access a DynamoDB table by creating a proxy for the DynamoDB query API.
API cache is not enabled for a method, it is enabled for a stage
API Gateway – Integrations (high level)
Lambda Function
Invoke Lambda function
Easy way to expose REST API backed by AWS Lambda
HTTP
Expose HTTP endpoints in the backend
Example: internal HTTP API on premise, Application Load Balancer…
Why? Add rate limiting, caching, user authentications, API keys, etc…
AWS Service
Expose any AWS API through the API Gateway
Example: start an AWS Step Function workflow, post a message to SQS
Why? Add authentication, deploy publicly, rate control…
API Gateway - Endpoint Types
Edge-Optimized (default)
For global clients
Requests are routed through the CloudFront edge locations (improves latency)
The API Gateway lives in only one region but it is accessible efficiently through edge locations
Regional
For clients within the same region
Could manually combine with your own CloudFront distribution for global deployment (this way you will have more control over the caching strategies and the distribution)
Private
Can only be accessed within your VPC using an Interface VPC endpoint (ENI)
Use resource policy to define access
API Gateway – Security
User Authentication through
IAM Roles (useful for internal applications)
Cognito (identity for external users – example mobile users)
Custom Authorizer (your own logic)
Custom Domain Name HTTPS
Security through integration with AWS Certificate Manager (ACM)
If using Edge-Optimized endpoint, then the certificate must be in us-east-1
If using Regional endpoint, the certificate must be in the API Gateway region
Must setup CNAME or A-alias record in Route 53
Access Management
IAM Policy
Create an IAM policy and attach to User or Role to allow it to call an API
Good to provide access within your own AWS account
Leverages Sig v4 where lAM credential are in the request headers
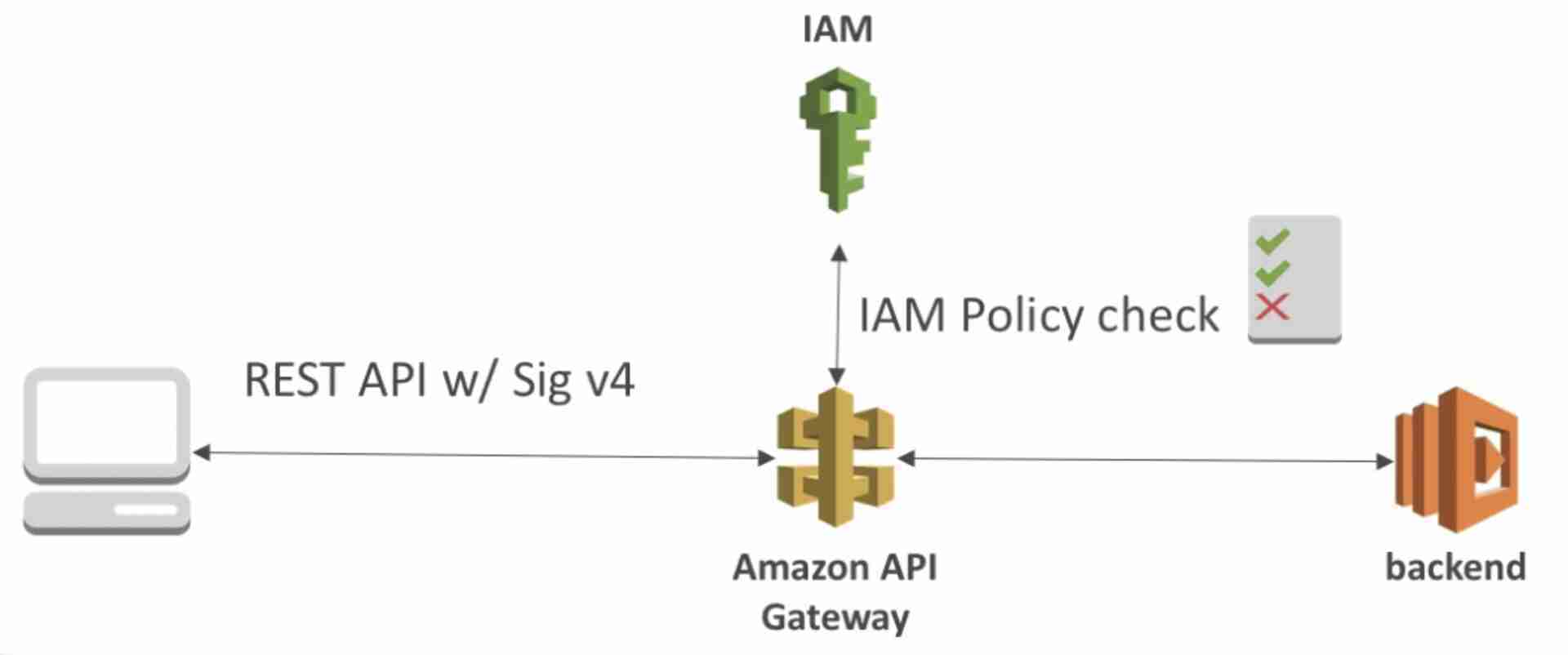
Lambda Authorizer
Uses a Lambda function to validate the token being passed in the header and return an lAM policy to determine if the user should be allowed to access the resource.
Option to cache result of authentication
For OAuth / SAML / 3rd party type of authentication
Good to provide access outside your AWS account if you have an existing IDP
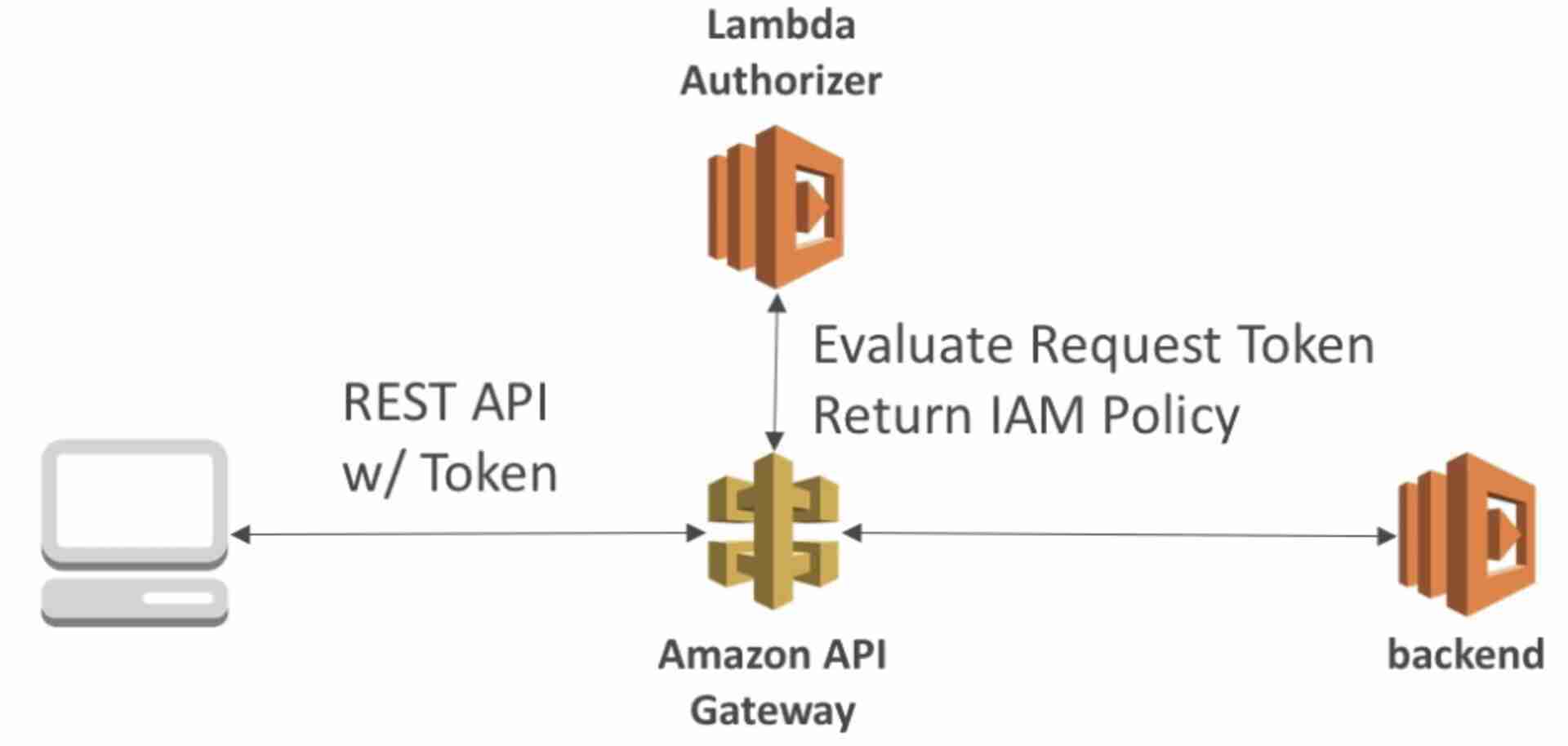
Cognito User Pools (CUP)
Seamless integration with CUP (no custom lambda implementation required)
Only supports authentication (authorization must be implemented in the backend)
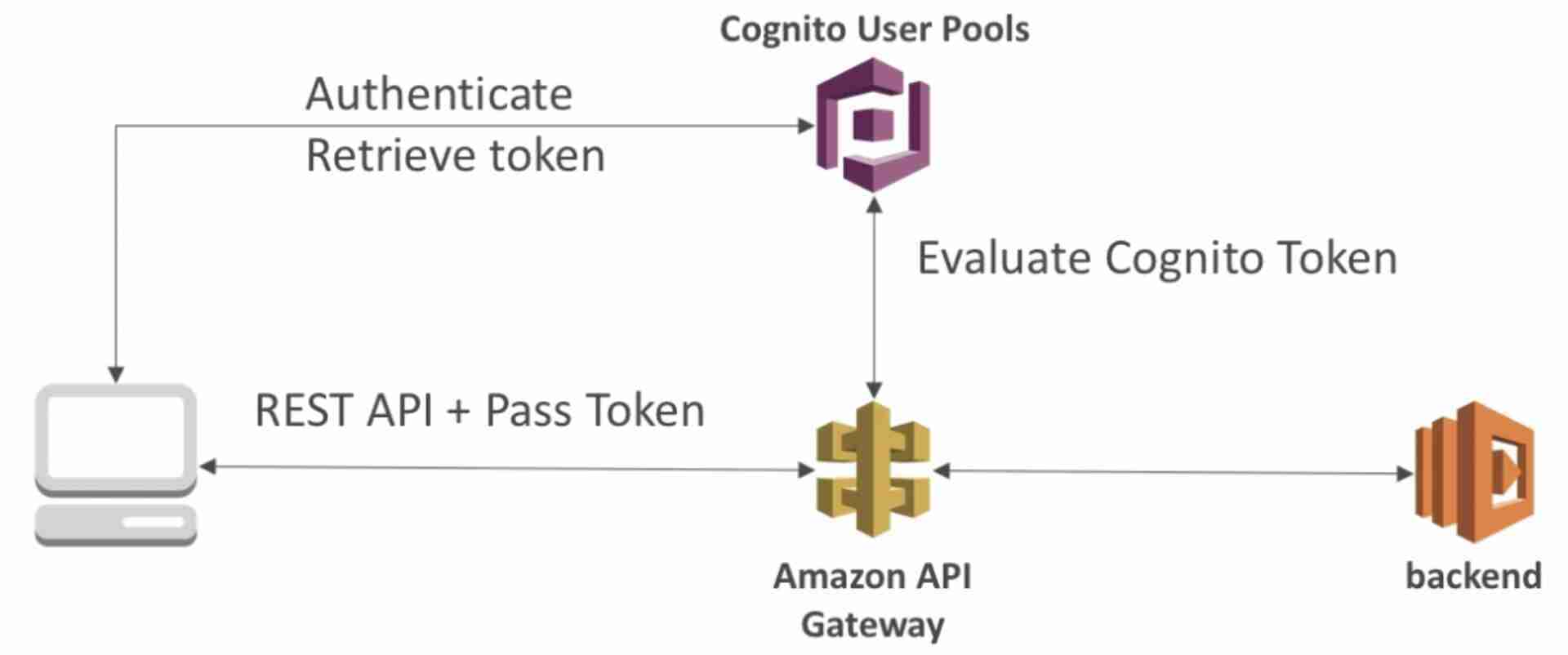
The client (user) first authenticates with Cognito and gets the access token which it passes in the header to API gateway. API gateway validates the token using Cognito and then hits the backend if the token is valid.
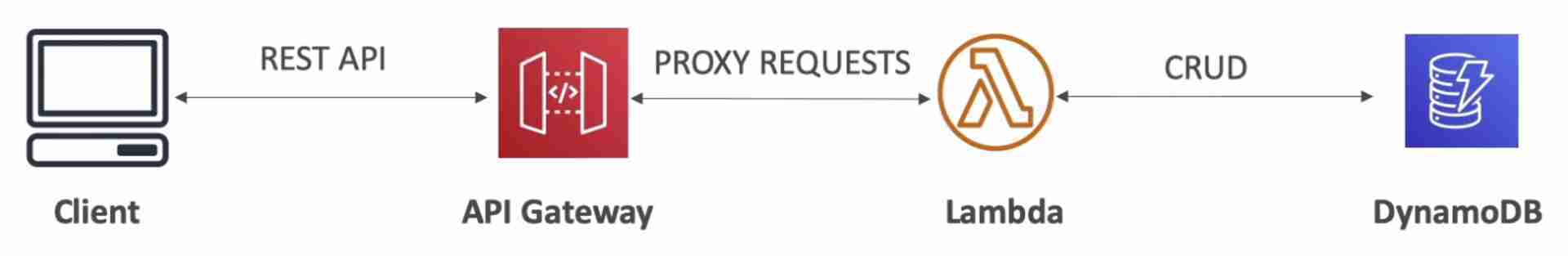
Serverless CRUD Application
AWS Step Functions
Build serverless visual workflow to orchestrate your Lambda functions
Features: sequence, parallel, conditions, timeouts, error handling, …
Can integrate with EC2, ECS, On -premises servers, API Gateway, SQS queues, etc …
Possibility of implementing human approval feature
Use cases: order fulfillment, data processing, web applications, any workflow
Amazon Cognito
Amazon Cognito lets you add user sign-up, sign-in, and access control to your web and mobile apps quickly and easily.
Amazon Cognito scales to millions of users and supports sign-in with social identity providers, such as Apple, Facebook, Google, and Amazon, and enterprise identity providers via SAML 2.0 and OpenID Connect.
Cognito User Pools:
Sign in functionality for app users
Integrate with API Gateway & Application Load Balancer
Cognito Identity Pools (Federated Identity):
Provide AWS credentials to users so they can access AWS resources directly
Integrate with Cognito User Pools as an identity provider
Cognito vs IAM: “hundreds of users”, ”mobile users”, “authenticate with SAML”
Cognito User Pools (CUP)
Serverless identity provider (provides sign in functionality for app users)
Create a serverless database of user for your web & mobile apps
Sends back a JSON Web Token (used to verify the identity of the user)
Simple login: Username (or email) / password combination
MFA support
Password reset
Supports Federated Identities allowing users to authenticate via third party identity provider like Facebook, Google, SAML, etc.
Seamless integration with API Gateway & ALB for authentication
Cognito Identity Pools (CIP) (Federated Identities)
Provides temporary credentials (using STS) to users so they can access AWS resources
Integrates with CUP as an identity provider
Users can then access AWS services directly or through API Gateway
The IAM policies applied to the credentials are defined in Cognito
They can be customized based on the user_id for fine grained control
Default IAM roles for authenticated and guest users
Example use case: provide temporary access to write to an S3 bucket after authenticating the user via FaceBook (using CUP identity federation)
- Can't use S3 pre-signed URL as we need to provide access to a bucket location and not an single object